A Vulnerability Scanner Which Uses It's Own
Protect Your Computer From Viruses Malware. See Whos Our Best Rated Antivirus Software.

The Pros And Cons Of Vulnerability Scanning Vulnerability Scan Pro
Ad 2022s Best Antivirus Review.
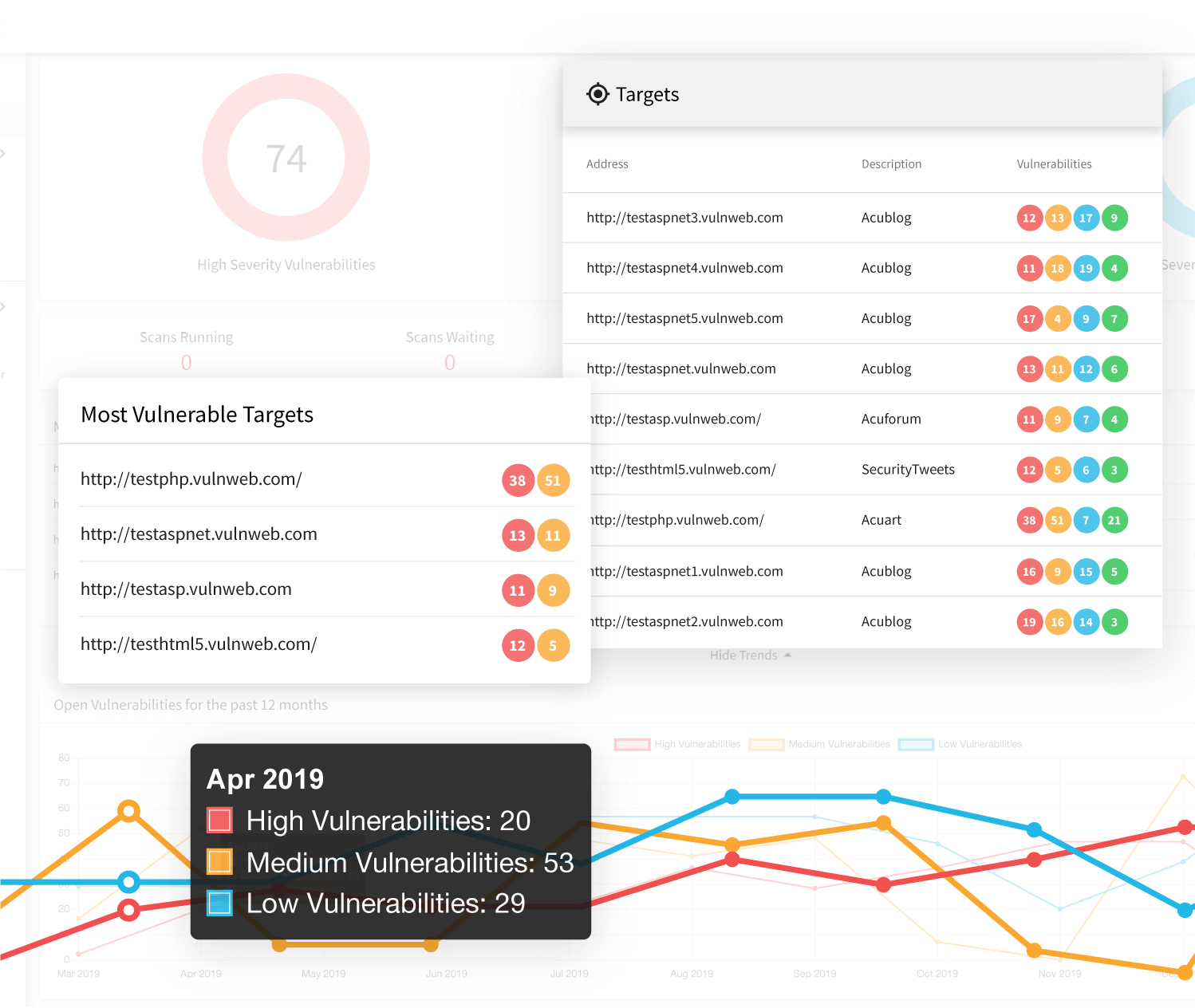
. Examples of these scanners are Tennables Nessus scanner. Create a target list or select one target scans then. Ad Comprehensive Antivirus Online Security Identity Theft Protection.
Scan systems in local network remote locations and closed network. Web Application Vulnerability Scanners are automated tools that scan web applications normally from the outside to look for security vulnerabilities such as Cross-site scripting SQL Injection. A vulnerability scanner is a software application that can be used to find security weaknesses in computers networks operating systems and other software.
Start Your Free Trial Today. Secure your cloud native applications. The insights you gain from.
Multiple Layers of Protection for Cyber Security. The Open Vulnerability Assessment System OpenVAS is a comprehensive open-source vulnerability scanning tool and vulnerability management system. Vulnerability scanners leverage automated tests to gather information about a network and identify security gaps that hackers can use to access it.
Enter the Pensive Security RPi Vulnerability Scanner. A vulnerability scanner is an automated vulnerability testing tool that monitors for misconfigurations or coding flaws that pose cybersecurity threats. Its free of cost and.
A Vulnerability Scanner Auto Exploiter You can use this tool to check the security May 01 2021 2 min read. Solve Your Toughest Network Problems With SolarWinds Advanced IP Scanner. Automatically detect vulnerabilities misconfigurations risky software and open ports.
A Network Vulnerability Scanner for All Environments. As a result the scan can cause issues such as errors and reboots. Solve Your Toughest Network Problems With SolarWinds Advanced IP Scanner.
Running a vulnerability scan can pose its own risks as it is inherently intrusive on the target machines running code. Ad Eliminate blind spots. Ad Detect Remediate Vulnerabilities Before Attackers Exploit Them.
By using a scanner you can be confident that your network is being. This is an integral component of a vulnerability management. Vulnerability scanning is the process of identifying security weaknesses and flaws in systems and software running on them.
Vulnerability scanning also commonly known as vuln scan is an automated process of proactively identifying network application and security vulnerabilities. Ad See Why Nessus Is 1 For Vulnerability Assessment - Start Your Free Trial Now. Ad Get To The Root Cause More Quickly With Intelligent Topology-Aware Network Alerts.
A vulnerability scanner is an automated tool that identifies and creates an inventory of all IT assets including servers desktops laptops virtual machines. Ad Snyk brings developers security together. April 24 2019.
What are vulnerability scanners. Ad Get To The Root Cause More Quickly With Intelligent Topology-Aware Network Alerts. We have developed a Raspberry Pi vulnerability scanner that is extremely easy to use just plug it into your router.
This is because its difficult to keep up with all the latest threats and know exactly what to look for. Let Us Help You Find The Perfect Antivirus. OpenVAS is a fully-featured vulnerability scanner that uses multiple scanning techniques to help organizations identify a wide range of internal and external vulnerabilities.
One of the most well known types of vulnerability scanners is perhaps the network vulnerability scanner. Snyk has powerful fix advice and automation that enables security at scale and speed. Leader in Vulnerability Risk Management Wave Report Q4 2019.

Top 10 Vulnerability Scanners Most Popular Scanners In 2022

Belum ada Komentar untuk "A Vulnerability Scanner Which Uses It's Own"
Posting Komentar